
IOM FIU Fraud by False Representation in Banking – a typology
08/02/2026
Introduction
- The Isle of Man FIU produces monthly typologies to improve understanding of financial crime risks, including money laundering (ML) and predicate offences like fraud.
- These are derived from Suspicious Activity Reports (SARs) and open-source intelligence (OSINT).
- This briefing focuses on "Fraud by False Representation," a common push payment fraud tactic where scammers impersonate trusted entities to deceive victims into authorising transactions. It is particularly relevant to banking professionals handling online and mobile banking services.
- This briefing draws directly from the FIU's January 2026 typology on this topic, emphasising proactive detection and reporting to mitigate losses and comply with regulatory obligations.
Summary of the Typology
- Fraud by false representation involves scammers posing as legitimate representatives (e.g., bank employees) to trick customers into revealing sensitive information or approving unauthorised transactions.
- In the FIU's example, this enables "push" fraud, where funds are transferred out of the victim's account via approved one-time passcodes (OTPs).
Key elements from the FIU analysis:
- Scammers use social engineering to gain trust, often referencing real transaction details to appear credible.
- Victims are manipulated into confirming OTPs, which grant access to banking apps or allow large transfers.
- Funds are typically sent to accounts in foreign jurisdictions, with mismatched IP logins indicating compromise.
- This typology aligns with broader efforts to identify ML threats and supports the development of targeted controls in the regulated sector.
Example Scenario
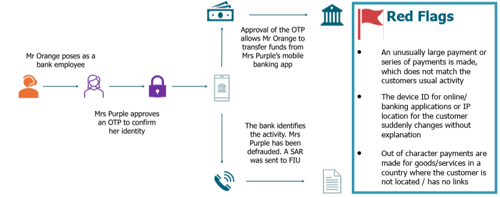
The following is a fictional but representative case from the FIU typology:
- Bank Notification: Blue Bank detects an unusually large payment of GBP 25,000.00 made via a customer's (Mrs Purple) banking app to a third-party account.
- Customer Contact: Upon verification, Mrs Purple denies knowledge of the transaction.
- Fraud Details: She reports being contacted by "Mr Orange," who claimed to be a Blue Bank employee. He referenced her recent transactions and requested OTP approval to "verify her identity."
- Compromise Mechanism: By approving the OTP, Mrs Purple unwittingly allowed Mr Orange to access her app and initiate the transfer.
- Indicators of Fraud: Login IP addresses from a foreign jurisdiction matched the recipient bank's sort code.
- Response: Blue Bank suspects app compromise and submits a SAR to the FIU.
This scenario illustrates how scammers exploit trust in banking processes to execute fraud, often resulting in rapid fund transfers that are hard to reverse.
Red Flags
Based on the FIU's indicators, monitor for the following warning signs, which may trigger enhanced due diligence or SAR filing:
- Unusual Transaction Patterns: An unusually large payment or series of payments that deviates from the customer's typical activity profile.
- Device or Location Changes: Sudden changes in device ID for online/mobile banking apps or IP locations without a plausible explanation (e.g., customer travel).
- Out-of-Character Activity: Payments for goods/services in a country where the customer has no known presence or connections.
Additional contextual red flags (inferred from the typology):
- Customer reports unsolicited calls from "bank representatives" requesting OTPs or sensitive details.
- Mismatched transaction details, such as funds sent to high-risk jurisdictions.
- Rapid escalation of transaction amounts following unusual logins.
Recommendations and Actions
To prevent and detect this fraud type:
- Enhance Customer Education: Remind customers never to share OTPs or approve codes requested over the phone/email. Use in-app alerts and awareness campaigns.
- Strengthen Authentication: Implement multi-factor checks for high-value transactions, including geolocation verification and behavioural biometrics.
- Monitoring and Alerts: Use transaction monitoring systems to flag anomalies in payment size, frequency, or login patterns. Set thresholds for automatic holds on suspicious transfers.
- Incident Response: Upon suspicion, immediately contact the customer for verification, freeze accounts if needed, and trace funds. Submit SARs promptly to the FIU or relevant authorities.
- Training: Conduct regular staff training on social engineering tactics and red flags. Simulate scenarios to improve response times.
- Collaboration: Share intelligence with industry peers and regulators to track emerging trends.
Reporting Obligations
- If fraud is suspected, file a SAR with the appropriate FIU or regulatory body without delay.
- Delaying could exacerbate losses and violate AML requirements.
SOURCE
Disclaimer: This briefing is for internal use and based on FIU-provided typologies. It does not constitute legal advice. Always consult regulatory guidelines for jurisdiction-specific requirements.
The Team
Meet the team of industry experts behind Comsure
Find out moreLatest News
Keep up to date with the very latest news from Comsure
Find out moreGallery
View our latest imagery from our news and work
Find out moreContact
Think we can help you and your business? Chat to us today
Get In TouchNews Disclaimer
As well as owning and publishing Comsure's copyrighted works, Comsure wishes to use the copyright-protected works of others. To do so, Comsure is applying for exemptions in the UK copyright law. There are certain very specific situations where Comsure is permitted to do so without seeking permission from the owner. These exemptions are in the copyright sections of the Copyright, Designs and Patents Act 1988 (as amended)[www.gov.UK/government/publications/copyright-acts-and-related-laws]. Many situations allow for Comsure to apply for exemptions. These include 1] Non-commercial research and private study, 2] Criticism, review and reporting of current events, 3] the copying of works in any medium as long as the use is to illustrate a point. 4] no posting is for commercial purposes [payment]. (for a full list of exemptions, please read here www.gov.uk/guidance/exceptions-to-copyright]. Concerning the exceptions, Comsure will acknowledge the work of the source author by providing a link to the source material. Comsure claims no ownership of non-Comsure content. The non-Comsure articles posted on the Comsure website are deemed important, relevant, and newsworthy to a Comsure audience (e.g. regulated financial services and professional firms [DNFSBs]). Comsure does not wish to take any credit for the publication, and the publication can be read in full in its original form if you click the articles link that always accompanies the news item. Also, Comsure does not seek any payment for highlighting these important articles. If you want any article removed, Comsure will automatically do so on a reasonable request if you email info@comsuregroup.com.


