
CRYPTO DEFI FLASH LOANS OFFER MONEY LAUNDERING OPPORTUNITIES
12/08/2025
Flash loans are a unique and powerful feature of decentralised finance (DeFi) that, while initially designed for legitimate use cases like arbitrage and collateral swaps, have increasingly drawn attention for their potential misuse—particularly in money laundering.
What Are Flash Loans?
- Flash loans allow users to borrow large amounts of cryptocurrency without collateral, under the condition that the loan is repaid within the same blockchain transaction.
- If the borrower fails to repay, the entire transaction is reverted, as if it never happened.
Flash Loans as a Money Laundering Tool
Here's how flash loans can be exploited for laundering:
- Instant Access to Capital
- Criminals can borrow millions in crypto without upfront capital, enabling large-scale operations.
- Complex Transaction Chains
- They can execute a series of rapid swaps across multiple DeFi protocols (e.g., DEXs, lending platforms), obfuscating the origin of funds.
- Atomic Execution
- Because everything happens in one transaction, there's no risk of default, and no need for trust between parties.
- Disconnection from Source
- After the loan is repaid, the remaining funds—often routed through mixers or privacy-enhancing protocols—appear "clean" and disconnected from their illicit origin.
- Automation via Smart Contracts
- These laundering operations can be fully automated, enabling industrial-scale laundering with minimal human oversight.
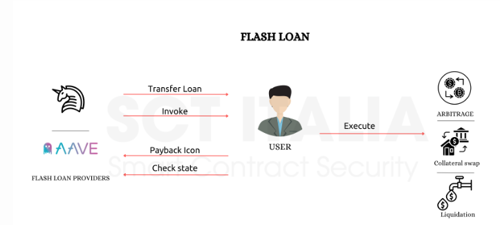
Flash Loan Laundering Flow (Described)
Here's a step-by-step breakdown of how a laundering operation might work using flash loans:
- Initiate Flash Loan
- A user borrows a large amount of crypto (e.g., ETH or stablecoins) from a DeFi protocol like Aave or dYdX.
- Execute Complex Swaps
- The borrowed funds are routed through multiple decentralised exchanges (DEXs), liquidity pools, or lending protocols, often using smart contracts to automate the process.
- Obfuscate Transaction Trail
- Funds may be split, swapped into privacy coins (e.g., Monero), or routed through mixers like Tornado Cash to obscure their origin.
- Repay Flash Loan
- The original loan is repaid within the same transaction block, leaving behind "cleaned" profits.
- Withdraw or Reinvest
- The remaining funds are either withdrawn to a new wallet or reinvested into other DeFi protocols, making tracing even harder.
Real-World Flash Loan Exploits
Here are some notable cases where flash loans were used for illicit or manipulative purposes:
Zunami Protocol Attack (2024)
- Attackers used flash loans to manipulate the price of Zunami’s stablecoin pools, draining over $2.1 million. The exploit involved:
- Borrowing funds via flash loan.
- Manipulating pool prices.
- Profiting from the arbitrage.
- Repaying the loan—all in one transaction
Themis Protocol Exploit
- A flash loan was used to manipulate collateral values in Themis, allowing the attacker to borrow more than they should have been able to.
- The attacker:
- Took a flash loan.
- Inflated the value of collateral.
- Borrowed against it.
- Repaid the flash loan and walked away with the excess.
Alpha Homora x Iron Bank Attack (2021)
- One of the largest flash loan exploits, where attackers used recursive borrowing and flash loans to drain $37 million.
- The exploit involved:
- Flash loans from multiple protocols.
- Recursive lending/borrowing loops.
- Exploiting a pricing oracle flaw.
Challenges for Regulators
- Lack of Intermediaries: No banks or centralised exchanges are involved, making traditional AML (Anti-Money Laundering) enforcement ineffective.
- Anonymity & Speed: Transactions are fast, pseudonymous, and often routed through privacy tools like Tornado Cash.
- Technical Complexity: The use of smart contracts and multi-protocol routing makes forensic tracing extremely difficult.
Mitigation Strategies
- On-chain analytics tools (e.g., Chainalysis, TRM Labs) are being developed to trace flash loan activity.
- Regulatory frameworks like the OECD's CARF aim to bring transparency to crypto transactions, though DeFi remains a grey area.
- Protocol-level safeguards (e.g., rate limits, transaction monitoring) are being explored to detect suspicious patterns.
Source
https://smartcontract.tips/en/post/flash-loans-attacks-mechanics-and-case-study
The Team
Meet the team of industry experts behind Comsure
Find out moreLatest News
Keep up to date with the very latest news from Comsure
Find out moreGallery
View our latest imagery from our news and work
Find out moreContact
Think we can help you and your business? Chat to us today
Get In TouchNews Disclaimer
As well as owning and publishing Comsure's copyrighted works, Comsure wishes to use the copyright-protected works of others. To do so, Comsure is applying for exemptions in the UK copyright law. There are certain very specific situations where Comsure is permitted to do so without seeking permission from the owner. These exemptions are in the copyright sections of the Copyright, Designs and Patents Act 1988 (as amended)[www.gov.UK/government/publications/copyright-acts-and-related-laws]. Many situations allow for Comsure to apply for exemptions. These include 1] Non-commercial research and private study, 2] Criticism, review and reporting of current events, 3] the copying of works in any medium as long as the use is to illustrate a point. 4] no posting is for commercial purposes [payment]. (for a full list of exemptions, please read here www.gov.uk/guidance/exceptions-to-copyright]. Concerning the exceptions, Comsure will acknowledge the work of the source author by providing a link to the source material. Comsure claims no ownership of non-Comsure content. The non-Comsure articles posted on the Comsure website are deemed important, relevant, and newsworthy to a Comsure audience (e.g. regulated financial services and professional firms [DNFSBs]). Comsure does not wish to take any credit for the publication, and the publication can be read in full in its original form if you click the articles link that always accompanies the news item. Also, Comsure does not seek any payment for highlighting these important articles. If you want any article removed, Comsure will automatically do so on a reasonable request if you email info@comsuregroup.com.


